This is the multi-page printable view of this section. Click here to print.
Concepts
- 1: Firewall
- 2: Linux FileSystem
- 2.1: Linux file system
- 3: Networking
- 4: Package Management
- 5: Storage
- 5.1: Storage
- 6: users
1 - Firewall
A firewall provides a means to protect machines from any unwanted traffic. It enables users/administrators to control incoming network traffic on host machines by defining a set of firewall rules. These rules are used to sort the incoming traffic and either block it or allow through.
firewalld
firewalldis a firewall service daemon that provides a dynamic customizable host-based firewall. Being dynamic, it enables creating, changing, and deleting the rules without the necessity to restart the firewall daemon each time the rules are changed.firewalld uses the concepts of zones and services
Zones are predefined sets of rules.
Network interfaces and sources can be assigned to a zone.
The traffic allowed depends on the network your computer is connected to and the security level this network is assigned.
Firewall services are predefined rules that cover all necessary settings to allow incoming traffic for a specific service and they apply within a zone.
Services use one or more ports or addresses for network communication.
Firewall filter communication based on ports.
# To start firewalld
systemctl unmask firewalld
systemctl enable firewalld.service
systemctl start firewalld
# To stop firewalld
systemctl stop firewalld
systemctl disable firewalld
systemctl mask firewalld
# Quick command to check whether the firewall is enabled or disabled
systemctl is-enabled firewalld
[root@centos8 ~]# systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2019-10-28 15:05:45 CET; 1min 25s ago
Docs: man:firewalld(1)
Main PID: 772 (firewalld)
Tasks: 2 (limit: 11525)
Memory: 36.2M
CGroup: /system.slice/firewalld.service
└─772 /usr/libexec/platform-python -s /usr/sbin/firewalld --nofork --nopid
Oct 28 15:05:44 centos8 systemd[1]: Starting firewalld - dynamic firewall daemon...
Oct 28 15:05:45 centos8 systemd[1]: Started firewalld - dynamic firewall daemon.
firewall-cmd
firewall-cmd is a cli for firewall service.
To get more details on how to use firewall-cmd : firewall-cmd --help
# Examples:
# How to add a service to firewall
yum install tftp-server
firewall-cmd --add-service=tftp
# How to add and open port to firewall
## The command below will open the port effective immediately, but will not persist across reboots:
firewall-cmd --add-port=<YOUR PORT>/tcp
## The following command will create a persistent rule, but will not be put into effect immediately:
firewall-cmd --permanent --add-port=<YOUR PORT>/tcp
Resources
firewalld(1) man page
firewalld.zone(5) man page
redhat-documentation
2 - Linux FileSystem
2.1 - Linux file system
sriram@sriram-Inspiron-5567:~$ sudo fdisk -l /dev/sda
Disk /dev/sda: 111,8 GiB, 120034123776 bytes, 234441648 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: gpt
Disk identifier: 833807FE-A7E1-46DA-B629-ECC1B32A087E
Device Start End Sectors Size Type
/dev/sda1 2048 1050623 1048576 512M EFI System
/dev/sda2 1050624 217874431 216823808 103,4G Linux filesystem
/dev/sda3 217874432 234440703 16566272 7,9G Linux swap
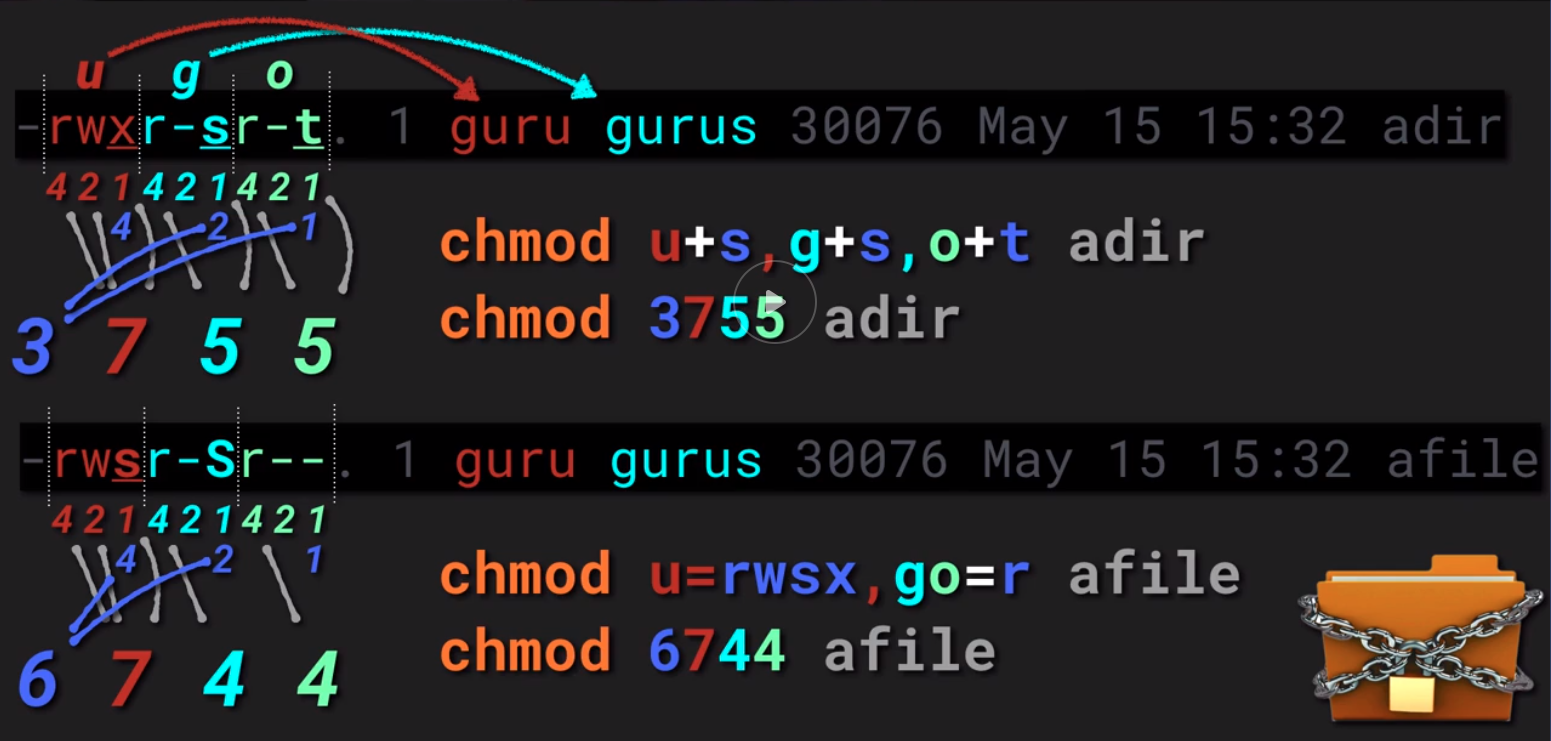
Linux File Permissions
-rwsrwsrwtchmod u+s,g+s,o+t dir
- Sticky bit
Items in directory may only be deleted by owner.
[root@10 ~]# ls -ld /tmp
drwxrwxrwt. 8 root root 216 Oct 27 11:18 /tmp
SGID - Set Group Identity
Can be set on directories aswell as on files Directory : New objects in this directory inherit its group ownership.
Execuable File : Runs as owning group rather than invoker’s group.SUID - Set User Identity
Executable: Program runs as owner, rather than caller.
References
Linux file system
man hier
3 - Networking
Warning
net-tools utilities are obsoleted by iproute2https://wiki.linuxfoundation.org/networking/iproute2
| Legacy utility | Replacement command | Note |
|---|---|---|
| ifconfig | ip addr, ip link, ip -s | Address and link configuration |
| route | ip route | Routing tables |
| arp | ip neigh | Neighbors |
| iptunnel | ip tunnel | Tunnels |
| nameif | ifrename, ip link set name | Rename network interfaces |
| ipmaddr | ip maddr | Multicast |
| netstat | ip -s, ss, ip route | Socket statistics |
ip address statistics with colors and human readable format
ip -stats -color -human addrip -s -c -h a
How to start/stop an interface
ifup eth0 (deprecated)
ifdown eth0 (deprecated)
To show the current neighbour table in kernel$ ip neigh
To temporarily assign IP Address to a specific network interface (eth0)$ sudo ip addr add 192.168.56.1 dev eth0
To remove an assigned IP address from an network interface (eth0)
$ sudo ip addr del 192.168.56.15/24 dev eth0
ethtool
a command line utility for querying and modifying network interface controller parameters and device drivers.$ sudo ethtool enp0s3
ping (Packet INternet Groper)
Utility normally used for testing connectivity between two systems on a network (Local Area Network (LAN) or Wide Area Network (WAN)). It uses ICMP (Internet Control Message Protocol) to communicate to nodes on a network.
To test connectivity to another node, simply provide its IP or host name, for example.$ ping 192.168.0.1
traceroute | tracepath
Traceroute is a command line utility for tracing the full path from your local system to another network system. It prints number of hops (router IP’s) in that path you travel to reach the end server. It is an easy-to-use network troubleshooting utility after ping command.
Tracepath is similar to traceroute but for non root users.
In this example, we are tracing the route packets take from the local system to one of Google’s servers with IP address 216.58.204.46.$ traceroute 216.58.204.46
If traceroute is not available on the system, then install the utility as a root : yum install traceroute
MTR - a network diagnostic tool
MTR is a modern command-line network diagnostic tool that combines the functionality of ping and traceroute into a single diagnostic tool. Its output is updated in real-time, by default until you exit the program by pressing q.
The easiest way of running mtr is to provide it a host name or IP address as an argument, as follows.
$ mtr google.com (or) $ mtr 216.58.223.78
route - show / manipulate the IP routing table
route is a command line utility for displaying or manipulating the IP routing table of a Linux system. It is mainly used to configure static routes to specific hosts or networks via an interface.
You can view Kernel IP routing table by typing.
$ route
Add a default gateway to the routing table.
$ sudo route add default gw <gateway-ip>
Add a network route to the routing table.
$ sudo route add -net <network ip/cidr> gw <gateway ip> <interface>
Delete a specific route entry from the routing table.
$ sudo route del -net <network ip/cidr>
nmcli - command line tool for network management
nmcli is an easy-to-use, scriptable command-line tool to report network status, manage network connections, and control the NetworkManager.
Install network-manager for nmcli:sudo apt install network-manager
To check network connections on your system$ nmcli con show
List out all network interfaces and status$ nmcli d (or) $ nmcli dev status
[root@10 ~]# nmcli d
DEVICE TYPE STATE CONNECTION
enp0s3 ethernet connected enp0s3
enp0s8 ethernet connected enp0s8
lo loopback unmanaged --
Warning
netstat is obsolete and replaced by ssAdditionally, it is also a fundamental network service debugging tool used to check which programs are listening on what ports. For instance, the following command will show all TCP ports in listening mode and what programs are listening on them. $ sudo netstat -tnlp
To view kernel routing table, use the -r flag (which is equivalent to running route command above). $ netstat -r
ss (socket statistics) - another utility to investigate sockets
ss (socket statistics) is a powerful command line utility to investigate sockets. It dumps socket statistics and displays information similar to netstat. In addition, it shows more TCP and state information compared to other similar utilities.
The following example show how to list all TCP ports (sockets) that are open on a server.$ ss -ta
nc (or netcat) - arbitrary TCP and UDP connections and listens
NC (NetCat) also referred to as the “Network Swiss Army knife”, is a powerful utility used for almost any task related to TCP, UDP, or UNIX-domain sockets.
- It can open TCP connections
- send UDP packets
- listen on arbitrary TCP and UDP ports
- do port scanning
- deal with both IPv4 and IPv6.
Example to show how to scan a list of ports.$ nc -zv www.google.com 21 22 80 443 3000
nc -zv www.google.com 21 22 80 443 3000
nc: connect to www.google.com port 21 (tcp) failed: Connection timed out
nc: connect to www.google.com port 21 (tcp) failed: Connection timed out
nc: connect to www.google.com port 22 (tcp) failed: Connection timed out
nc: connect to www.google.com port 22 (tcp) failed: Connection timed out
Connection to www.google.com 80 port [tcp/http] succeeded!
Connection to www.google.com 443 port [tcp/https] succeeded!
nc: connect to www.google.com port 3000 (tcp) failed: Connection timed out
You can also specify a range of ports as shown.$ nc -zv www.google.com 20-90
The following example shows how to use nc to open a TCP connection to port 5000 on server2.tecmint.lan, using port 3000 as the source port, with a timeout of 10 seconds.$ nc -p 3000 -w 10 server2.tecmint.lan 5000
nmap
Nmap (Network Mapper) is a powerful and extremely versatile tool for Linux system/network administrators. It is used gather information about a single host or explore networks an entire network. Nmap is also used to perform security scans, network audit and finding open ports on remote hosts and so much more.
You can scan a host using its host name or IP address, for instance.
$ nmap google.com
Find all devices connected to the same Network using nmap
~$ nmap -sP 192.168.2.1/24
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-04 22:14 CEST
Nmap scan report for wn3000rpv3.home (192.168.2.1)
Host is up (0.098s latency).
Nmap scan report for 192.168.2.6 (192.168.2.6)
Host is up (0.098s latency).
Nmap scan report for 192.168.2.11 (192.168.2.11)
Host is up (0.011s latency).
Nmap scan report for sriram-inspiron-5567.home (192.168.2.13)
Host is up (0.00024s latency).
Nmap scan report for 192.168.2.40 (192.168.2.40)
Host is up (0.064s latency).
Nmap scan report for router.home (192.168.2.254)
Host is up (0.088s latency).
Nmap done: 256 IP addresses (6 hosts up) scanned in 11.17 seconds
DNS Lookup Utilities
host command is a simple utility for carrying out DNS lookups, it translates host names to IP addresses and vice versa.$ host google.com
dig (domain information groper) is also another simple DNS lookup utility, that is used to query DNS related information such as A Record, CNAME, MX Record etc, for example:$ dig google.com
Nslookup is also a popular command line utility to query DNS servers both interactively and non-interactively. It is used to query DNS resource records (RR). You can find out “A” record (IP address) of a domain as shown.$ nslookup google.com
tcp dump
Linux Network Packet Analyzers: Tcpdump is a very powerful and widely used command-line network sniffer. It is used to capture and analyze TCP/IP packets transmitted or received over a network on a specific interface.
To capture packets from a given interface, specify it using the -i option.$ tcpdump -i eth1
To capture a specific number of packets, use the -c option to enter the desired number.$ tcpdump -c 5 -i eth1
To capture and save packets to a file for later analysis, use the -w flag and specify the output file.$ tcpdump -w captured.pacs -i eth1
References
4 - Package Management
4.1 - apk
Alpine is the light weight linux distribution. Alpine uses apk as the package manager.
References
4.2 - deb
The major reason to use apt tools though is for the dependency management. The apt tools understand that in order to install a given package, other packages may need to be installed too, and apt can download these and install them, whereas dpkg does not.
References
4.3 - dnf
DNF or Dandified yum is the next generation version of yum, a package manager for RPM-based Linux distributions like fedora,centos and redhat.
dnf -h
dnf --help
[root@192 ~]# dnf history
ID | Command line | Date and time | Action(s) | Altered
-------------------------------------------------------------------------------
5 | install transmission-gtk | 2020-07-17 13:26 | Install | 3
4 | install epel-release | 2020-07-17 13:25 | Install | 1
3 | | 2020-07-17 11:33 | Install | 8
2 | | 2020-07-17 11:27 | Removed | 1
1 | | 2020-07-17 11:15 | Install | 1476 EE
[root@192 ~]# dnf repolist
repo id repo name
AppStream CentOS-8 - AppStream
BaseOS CentOS-8 - Base
epel Extra Packages for Enterprise Linux 8 - x86_64
epel-modular Extra Packages for Enterprise Linux Modular 8 - x86_64
extras CentOS-8 - Extras
google-chrome google-chrome
#search package details for the given string
[root@192 ~]# dnf search chrome
Last metadata expiration check: 0:31:24 ago on Fri 17 Jul 2020 01:25:55 PM CEST.
======================================== Name & Summary Matched: chrome ========================================
google-chrome-stable.x86_64 : Google Chrome
google-chrome-beta.x86_64 : Google Chrome (beta)
google-chrome-unstable.x86_64 : Google Chrome (unstable)
chromedriver.x86_64 : WebDriver for Google Chrome/Chromium
============================================= Name Matched: chrome =============================================
chrome-gnome-shell.x86_64 : Support for managing GNOME Shell Extensions through web browsers
mathjax-winchrome-fonts.noarch : Fonts used by MathJax to display math in the browser
=========================================== Summary Matched: chrome ============================================
webextension-token-signing.x86_64 : Chrome and Firefox extension for signing with your eID on the web
# clear all cached packages from the system
[root@192 ~]# dnf clean all
44 files removed
References
4.4 - rpm
4.5 - yum
yum is broken on the server
### YUM not working on Centos and gave below error
could not retrieve mirrorlist http://mirrorlist.centos.org/?release=7&arch=x86_64&repo=extras&infra=stock error was
14: curl#6 - "Could not resolve host: mirrorlist.centos.org; Unknown error"
### To Fix above issue : go to /etc/resolve.conf and add/update nameserver
nameserver 8.8.8.8
Fix : Rebuild the yum database
yum clean all
rm -f /var/lib/rpm/__db*
rpm --rebuilddb
yum update
5 - Storage
5.1 - Storage
# from baremetal
sriram@sriram-Inspiron-5567:~$ sudo fdisk -l /dev/sda
Disk /dev/sda: 111,8 GiB, 120034123776 bytes, 234441648 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: gpt
Disk identifier: 833807FE-A7E1-46DA-B629-ECC1B32A087E
Device Start End Sectors Size Type
/dev/sda1 2048 1050623 1048576 512M EFI System
/dev/sda2 1050624 217874431 216823808 103,4G Linux filesystem
/dev/sda3 217874432 234440703 16566272 7,9G Linux swap
# From Virtual Machine
[root@CentosServer1910 ~]# fdisk -l
Disk /dev/sda: 10 GiB, 10737418240 bytes, 20971520 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0xec47036c
Device Boot Start End Sectors Size Id Type
/dev/sda1 * 2048 2099199 2097152 1G 83 Linux
/dev/sda2 2099200 20971519 18872320 9G 8e Linux LVM
Disk /dev/mapper/cl_centosserver1910-root: 8 GiB, 8585740288 bytes, 16769024 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk /dev/mapper/cl_centosserver1910-swap: 1 GiB, 1073741824 bytes, 2097152 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
UUID - Get the uuid of devices on linux
UUID is the universally unique identifier that is assigned to devices on a linux system for the purpose of identification.
For example if your hard disk has 3 partitions then each partition is a device and has a uuid.
To find the uuid of devices connected to a system use the command ls -l /dev/disk/by-uuid/
[sriram@CentosServer1910 ~]$ ls -l /dev/disk/by-uuid/
total 0
lrwxrwxrwx. 1 root root 10 Nov 3 12:55 64b6f04f-d510-4c39-9a37-cacfeeec774b -> ../../sda1
lrwxrwxrwx. 1 root root 10 Nov 3 12:55 860d422d-1b58-4545-a139-10ffc6677f63 -> ../../dm-1
lrwxrwxrwx. 1 root root 10 Nov 3 12:55 86f561ac-6bdf-4768-8cdd-4333d6e74b47 -> ../../dm-0
Another command to find UUI : blkid
# from baremetal
sriram@sriram-Inspiron-5567:~$ sudo blkid
/dev/sda1: UUID="5FAA-9D41" TYPE="vfat" PARTLABEL="EFI System Partition" PARTUUID="80a7a0c8-1f77-45b0-b720-93a044c6b597"
/dev/sda2: UUID="17e11c76-30e6-4e5d-84ee-9ad13021351b" TYPE="ext4" PARTUUID="2376aa03-2148-4b8c-92c5-c0a40a3124a3"
/dev/sda3: UUID="170ab405-c120-4c49-a8cd-24a0b2bf346d" TYPE="swap" PARTUUID="ed20cc7f-76de-4371-8016-e10c030c1ef8"
# from virtual server
[sriram@CentosServer1910 ~]$ blkid
/dev/mapper/cl_centosserver1910-root: UUID="86f561ac-6bdf-4768-8cdd-4333d6e74b47" TYPE="xfs"
/dev/sda2: UUID="wi21xh-Sj3l-ocKe-Q6Qr-aRLv-n3Nm-hcYhL5" TYPE="LVM2_member" PARTUUID="ec47036c-02"
To get the uuid of a specific device, simply put the device name next to blkid : blkid /dev/sda1
[sriram@CentosServer1910 ~]$ sudo blkid /dev/sda*
/dev/sda: PTUUID="ec47036c" PTTYPE="dos"
/dev/sda1: UUID="64b6f04f-d510-4c39-9a37-cacfeeec774b" TYPE="ext4" PARTUUID="ec47036c-01"
/dev/sda2: UUID="wi21xh-Sj3l-ocKe-Q6Qr-aRLv-n3Nm-hcYhL5" TYPE="LVM2_member" PARTUUID="ec47036c-02"
6 - users
How to create a non-login user?
- Create user with -M (caps) flag.
- Lock the account to prevent from login
useradd -M subversion
usermod -L subversion
How to create a system user ?
$ adduser --system -s usr/sbin/nologin subversion
# The -r flag will create a system user - one which does not have a password, a home dir and is unable to login.
# -s flag is for shell , /bin/nologin prevents to have a shell for this user.
## Testing
$ sudo adduser --system --no-create-home --shell /usr/sbin/nologin subversion
Adding system user `subversion' (UID 109) ...
Adding new user `subversion' (UID 109) with group `nogroup' ...
Not creating home directory `/home/subversion'.
$ sudo grep subversion /etc/passwd /etc/shadow
/etc/passwd:subversion:x:109:65534::/home/subversion:/usr/sbin/nologin
/etc/shadow:subversion:*:18628:0:99999:7:::
## Check if account is usuable
$ sudo -u subversion whoami
subversion
$ sudo -u subversion date
Fri 01 Jan 2021 07:35:20 PM CET